Layer-2 Switching
Layer-2 switching is hardware-based, which means it uses the MAC address from the host’s NIC cards to filter the network. Switches use Application-Specific Integrated Circuits (ASICs) to build and maintain filter tables.
Layer-2 switches are fast because they do not look at the Network layer header information, looking instead at the frame’s hardware addresses before deciding to either forward the frame or drop it.
Layer-2 switching provides the following:
Hardware-based bridging (MAC)
Wire speed
Low latency
Low cost
What makes layer-2 switching so efficient is that there is no modification to the data packet, only to the frame encapsulating the packet. Since no modification of the data packet is performed, the switching process is Faster and less error-prone than routing.
Three Switch Functions at Layer 2
There are three distinct functions of layer-2 switching:
Address learning
Layer-2 switches and bridges remember the source hardware address of each frame received on an interface and enter this information into a MAC database.
Forward/filter decisions
When a frame is received on an interface, the switch looks at the destination hardware address and finds the exit interface in the MAC database.
Loop avoidance
If multiple connections between switches are created for redundancy, network loops can occur. The panning-Tree Protocol (STP) is used to stop network loops and allow redundancy.
Address Learning
When a switch is powered on, the MAC filtering table is empty. When a device transmits and an interface receives a frame, the switch places the source address in the MAC filtering table, remembering what interface the device is located on. The switch has no choice but to flood the network with this frame because it has no idea where the destination device is located. If a device answers and sends a frame back, then the switch will take the source address from that frame and place the MAC address in the database, associating this address with the interface that received the frame. Since the switch now has two MAC addresses in the filtering table, the devices can make a point-to-point connection, and the frames will only be forwarded between the two devices. This is what makes layer-2 switches better than hubs. In a hub network, all frames are forwarded out all ports every time.
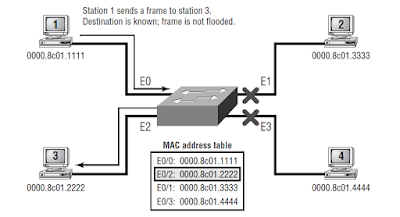
Figure 1.1 shows the procedures for how a MAC database is built.
FIGURE 1. 1 How switches learn hosts’ locations
BGP and RIP/EIGRP Split-Horizon Rule.
In this figure, there are four hosts attached to a switch. When the switch is powered on, it has nothing in the MAC address table.
1. Host 1 sends a frame to Host 3. Host 1’s MAC address is 0000.8c01.1111; Host 3’s MAC address is 0000.8c01.2222.
2. The switch receives the frame on the E0/1 interface (interface addressing is covered in Appendix B) and places the source address in the MAC address table.
3. Since the destination address is not in the MAC database, the frame is forwarded out all interfaces.
4. Host 3 receives the frame and responds to Host 1. The switch receives this frame on interface E0/3 and places the source hardware address in the MAC database.
5. Host 1 and Host 3 can now make a point-to-point connection and only the two devices will receive the frames. Hosts 2 and 4 will not see the frames.
If the two devices do not communicate to the switch again within a certain amount of time, the switch will flush the entries from the database to keep it as current as possible.
Forward/Filter Decisions
When a frame arrives at a switch interface, the destination hardware address is compared to the forward/filter MAC database. If the destination hardware address is known and listed in the database, the frame is only sent out the correct exit interface. The switch does not transmit the frame out any interface except for the destination interface. This preserves bandwidth on the other network segments and is called frame filtering.
If the destination hardware address is not listed in the MAC database, then the frame is broadcasted out all active interfaces except the interface the frame was received on. If a device answers the broadcast, the MAC database is updated with the device location (interface).
Loop Avoidance
Redundant links are a good idea between switches. They are used to help stop complete network failures if one link fails. Even though redundant links are extremely helpful, they cause more problems than they solve. Because frames can be broadcast down all redundant links simultaneously, network loops can occur, among other problems. Some of the most serious problems are discussed in the following list.
1.If no loop avoidance schemes are put in place, the switches will flood broadcasts endlessly throughout the internetwork. This is sometimes referred to as a broadcast storm. Figure 1.2 shows how a broadcast may be propagated throughout the network. Notice in the figure how a frame is continually broadcast through the internetwork Physical network.
FIGURE 1.2 Broadcast storms
2.A device can receive multiple copies of the same frame since the frame can arrive from different segments at the same time. Figure 2.3 shows how multiple frames can arrive from multiple segments simultaneously.
FIGURE 1.3 Multiple frame copies
3.The MAC address filter table will be confused about where a device is located since the switch can receive the frame from more than one link. It is possible that the switch can’t forward a frame because it is constantly updating the MAC filter table with source hardware address locations. This is called thrashing the MAC table.
4.One of the biggest problems is multiple loops generating throughout an internetwork. This means that loops can occur within other loops. If a broadcast storm were to then occur, the network would not be able to perform packet switching.
The Spanning-Tree Protocol, discussed soon that was developed to solve the problems presented in this list.
Related Links
BGP and RIP/EIGRP Split-Horizon Rule.



No comments:
Post a Comment